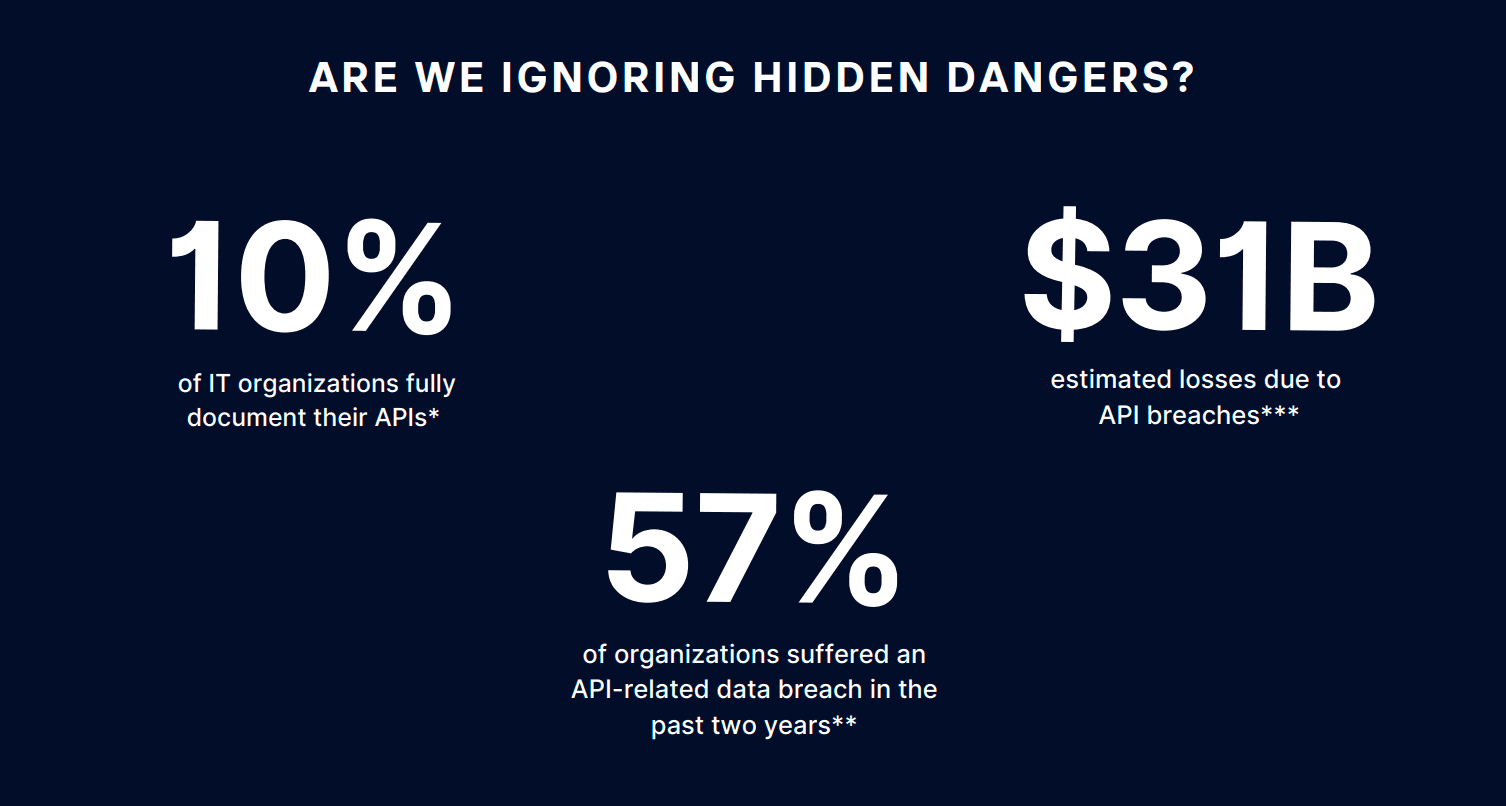
In today's interconnected world, remote desktop access tools like VNC (Virtual Network Computing) have become essential for businesses and individuals alike. However, VNC security vulnerabilities pose significant risks that can compromise sensitive data and system integrity. Understanding these vulnerabilities is crucial to ensuring the security of your digital infrastructure.
VNC allows users to control remote computers over a network connection, making it an invaluable tool for remote work, IT support, and system administration. Despite its benefits, VNC is not without flaws. Cybercriminals frequently exploit VNC security vulnerabilities to gain unauthorized access to systems, steal data, and disrupt operations.
In this comprehensive guide, we will delve into the most common VNC security vulnerabilities, explore their implications, and provide actionable solutions to safeguard your systems. By the end of this article, you will have a thorough understanding of how to protect your VNC setup from potential threats.
Read also:Is Laramie Doc Shaw Still Alive Uncovering The Truth Behind The Legend
Table of Contents
- Introduction to VNC
- VNC Security Vulnerabilities
- Common VNC Security Vulnerabilities
- Impact of VNC Security Vulnerabilities
- Best Practices for Securing VNC
- Tools for VNC Security
- Case Studies of VNC Security Breaches
- The Future of VNC Security
- Conclusion
Introduction to VNC
VNC is a graphical desktop sharing system that allows users to remotely control another computer. It transmits keyboard and mouse events from one computer to another, enabling real-time interaction with the remote system. VNC operates over a network and is widely used in various industries for remote work, troubleshooting, and collaboration.
While VNC offers convenience and efficiency, its security vulnerabilities have become a growing concern. Cyberattacks targeting VNC systems have increased in frequency and sophistication, making it imperative for organizations to prioritize VNC security.
VNC Security Vulnerabilities
VNC security vulnerabilities arise from a combination of factors, including misconfigurations, outdated software, and inadequate security measures. These vulnerabilities can be exploited by attackers to gain unauthorized access to systems, steal sensitive information, and cause significant damage.
Understanding these vulnerabilities is the first step in mitigating risks and ensuring the security of your VNC setup. In the following sections, we will explore the most common VNC security vulnerabilities and their potential impact.
Common VNC Security Vulnerabilities
Weak Passwords
One of the most prevalent VNC security vulnerabilities is the use of weak passwords. Attackers often employ brute-force attacks to guess passwords and gain access to VNC systems. Weak passwords, such as "123456" or "password," are easily compromised and provide little protection against unauthorized access.
Unencrypted Connections
Another critical vulnerability is the use of unencrypted VNC connections. Without encryption, data transmitted between the local and remote systems is susceptible to interception and eavesdropping. Attackers can capture sensitive information, such as login credentials and confidential files, by monitoring unencrypted VNC traffic.
Read also:Shatrughan Sinha Age A Comprehensive Look At The Iconic Bollywood Star
Default Ports
Many VNC installations use default ports, such as port 5900, for communication. This makes it easier for attackers to identify and target VNC systems. By scanning for open ports, cybercriminals can locate vulnerable VNC servers and exploit them to gain unauthorized access.
Impact of VNC Security Vulnerabilities
The consequences of VNC security vulnerabilities can be severe, ranging from data breaches to complete system compromise. Organizations may suffer financial losses, reputational damage, and legal liabilities as a result of these breaches. Additionally, individuals using VNC for personal purposes may face identity theft and privacy violations.
Understanding the potential impact of VNC security vulnerabilities is crucial for developing effective mitigation strategies. By addressing these risks proactively, organizations and individuals can protect their systems and data from malicious actors.
Best Practices for Securing VNC
Strong Authentication
Implementing strong authentication mechanisms is one of the most effective ways to secure VNC. This includes using complex passwords, enabling two-factor authentication (2FA), and regularly updating credentials. Strong authentication reduces the likelihood of unauthorized access and enhances overall system security.
Encryption
Encrypting VNC connections is essential for protecting sensitive data during transmission. Modern VNC clients and servers support encryption protocols, such as TLS and SSH, which can be configured to secure communication. By encrypting VNC traffic, organizations can prevent data interception and ensure the confidentiality of transmitted information.
Firewall Configuration
Configuring firewalls to restrict access to VNC ports is another critical best practice. By limiting access to trusted IP addresses and disabling unnecessary ports, organizations can reduce the attack surface and protect their VNC systems from unauthorized access.
Tools for VNC Security
Several tools and technologies are available to enhance VNC security. These include intrusion detection systems (IDS), network monitoring tools, and security information and event management (SIEM) solutions. By leveraging these tools, organizations can detect and respond to potential threats in real-time, minimizing the risk of security breaches.
Additionally, using VNC clients and servers with built-in security features, such as encryption and authentication, can further strengthen the security of VNC systems.
Case Studies of VNC Security Breaches
Real-world examples of VNC security breaches highlight the importance of addressing VNC security vulnerabilities. For instance, in 2020, a major healthcare provider suffered a data breach due to an unsecured VNC server, resulting in the exposure of sensitive patient information. Similarly, a financial institution experienced a significant security incident when attackers exploited weak VNC passwords to gain access to their systems.
These case studies underscore the need for robust VNC security measures and serve as a reminder of the potential consequences of neglecting VNC security vulnerabilities.
The Future of VNC Security
As technology continues to evolve, so do the threats targeting VNC systems. The future of VNC security lies in adopting advanced security measures, such as artificial intelligence (AI)-powered threat detection and zero-trust architectures. These innovations will help organizations stay ahead of emerging threats and ensure the security of their VNC setups.
Additionally, ongoing education and awareness programs can empower users to recognize and mitigate VNC security risks, fostering a culture of security within organizations.
Conclusion
VNC security vulnerabilities pose significant risks to organizations and individuals relying on remote desktop access. By understanding these vulnerabilities and implementing best practices, such as strong authentication, encryption, and firewall configuration, you can protect your systems and data from potential threats.
We encourage you to take action by reviewing your VNC setup, updating security measures, and staying informed about the latest developments in VNC security. Share your thoughts and experiences in the comments below, and explore our other articles for more insights into cybersecurity best practices.